Get Private Key?
Firstly published version of CryptoLocker virus was found on 5 September and has so far, according to BBC news, infected 250,000 PCs, approximately quarter of a million Windows computers across the world.
It is a ransomware that collects money through illegal way by encrypting victims’ files. The amount of money is at least 100 in all currency. According to CryptoLocker’s threatening message, the amount of money is in exchange for the private key copied once on its server, any delay in submission and removal of CryptoLocker will lead to the destruction of the key, which leads to impossibility to restore encrypted files forever.
As a matter of fact, the submission of money has not yet been known to lead to the acquirement of private keys claimed to be able to help retrieve encrypted data. Then how to get private keys?
One – by tracing where the public key was downloaded from.
The server an infected computer connects to is a local proxy which doesn't contain the private key.
Two – by arresting cyber criminal and getting private keys from them.
To escape easy arrest after the high exposure of CryptoLocker virus, the cyber criminal backstage usually attacks several machines in different regions/countries to jointly play a part in the operation of CryptoLocker affection. That is to say, the criminals' command and control server is given away via a second or third machine, which does post great difficulty for local law enforcement to seize the command and control server, because it takes them time to get there.
Three – by using cryptology to help decipher encrypted data.
CryptoLocker virus is designed to adopt well-established form of asymmetric encryption - a "public key" to encrypt the data, and a "private key" to decrypt it. Unfortunately the "public key" is programmed with strong third-party certified cryptography offered by Microsoft's CryptoAPI. Just like what Ryan Rubin, MD of global risk consultancy Protiviti says “unless you have the key, you simply cannot unlock the data that is encrypted".
 Do not pay the amount of money so fix on the message the moment you finish the preceding paragraphs. Perhaps, your data is worth more than the money you are asked to pay. But think about it, you are dealing with criminals who have already known that your computer is vulnerable and susceptible to virus, what is to guarantee that they will not do it again? Besides, one more submission of money is encouraging the criminals and funding them to spreading vicious codes to a broader mass and hence helping form a vicious circle. The right thing to do after being blackmailed by CryptoLocker virus is to remove supported infection and learn how to prevent from such scenario and enhance computer security thereafter. Let’s keep reading. If you have any questions, welcome to consult VilmaTech Online Support.
Do not pay the amount of money so fix on the message the moment you finish the preceding paragraphs. Perhaps, your data is worth more than the money you are asked to pay. But think about it, you are dealing with criminals who have already known that your computer is vulnerable and susceptible to virus, what is to guarantee that they will not do it again? Besides, one more submission of money is encouraging the criminals and funding them to spreading vicious codes to a broader mass and hence helping form a vicious circle. The right thing to do after being blackmailed by CryptoLocker virus is to remove supported infection and learn how to prevent from such scenario and enhance computer security thereafter. Let’s keep reading. If you have any questions, welcome to consult VilmaTech Online Support.How CryptoLocker Virus Affects?
According to Sarah Flanders, a 35-year-old charity worker from north London, she got infected by CryptoLocker virus after clicking open an email from the bank looked innocent enough from paymentsadmin@lloydsplc.co.uk. A software contained in the email immediately began encrypting every file on her computer from precious family photos to private correspondence and work documents. In just a short time all her files were blocked, and then a frightening message flashed up on her screen: "Your personal files have been encrypted and you have 95 hours to pay us $300."
In most cases, CryptoLocker virus is distributed via Trojan Horse Gameover Zeus that attacks vulnerable emails and fakes innocent-looking emails claiming a problem clearing a cheque is confirmed to random mass. One single click on content contained within will finally lead to the installation of Cryptolocker virus.
There are other dissemination routines that should be brought into your knowledge for future prevention:
- Drive-by download - freeware and shareware are the two types of programs that have obtained most favor by PC users and it is they that are targeted by and easily taken advantage of by deadly virus like Cryptolocker. What’s worse, PC users are prone to adopt “recommended” installation manner that usually contribute to unwitting installations of additional items.
- World Wide Web – it is not strange to hear that visiting porn sites and any other compromised web sites finally leads to a blocked computer.
- Spam adware – there have been a lot of spam ads popping up to help spread vicious codes by displaying alluring contents to trap clicks that would bring directly vicious codes.
- Vulnerable computer – ransomware like Cryptolocker virus is equipped with sniffer which is served to locate vulnerability and prepare for infiltration.
Recommendations
One - CryptoLocker Virus Needs to be Removed
Remove CryptoLocker virus is not the same as decipher data. It should be cleared that CryptoLocker is geared by Trojan horse, the one specializes in opening backdoor, compromising security and displays the block message. To make the threatening message gone and more importantly prevent further infections from exploiting the backdoor to initiate destructive infiltration, it is wise to remove CryptoLocker virus.
Two – Back up Information Regularly and Make Documents in Duplicate
In the age of ransomware plague, it is advisable to back up your documents and important information onto several other devices. It is also good when you are not around the computer where documents are originally created but access is required.
Considering the fact that anti-virus programs are disabled to help remove CryptoLocker virus, manual method is recommended to be involved. Below is the step to follow up. Should you have problems in proceeding the procedure, you are welcome to get professional help from VilmaTech online experts with rich virus removing experience.
Guide on Removing CryptoLocker Step by Step
For Windows Users
1. Log into Safe Mode with Networking.
- If you are using Windows 7, XP & Vista:
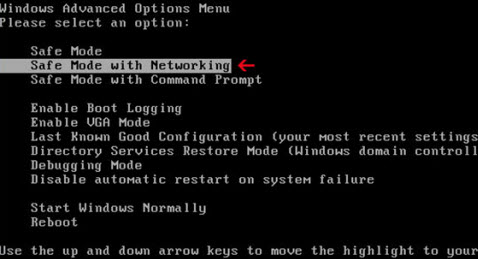
- If you are using Windows 8:
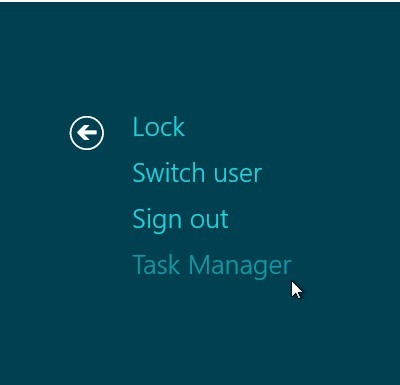
b: You will get three options there: Sleep, Shut down and Restart. Click on Restart option.

c: The next window says ‘Choose an Option’ screen,” then you need select “Troubleshoot.”
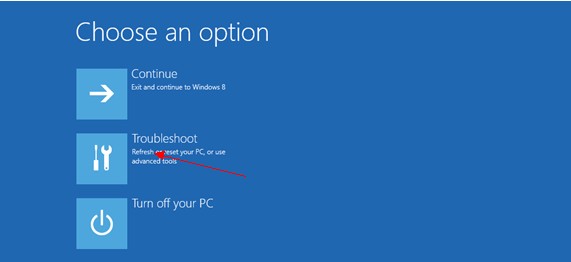
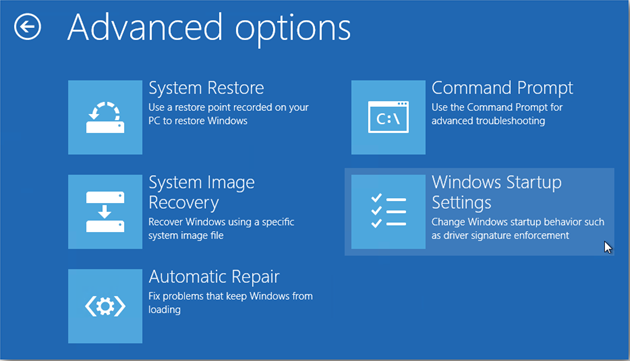
d: On the troubleshoot page click on ‘Advanced Options’. In the following window choose ‘startup settings
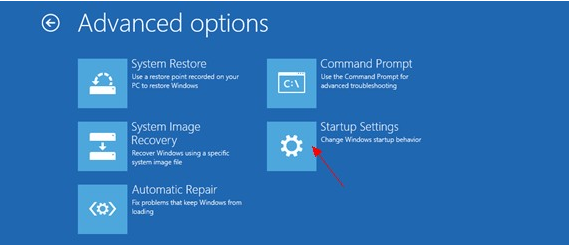
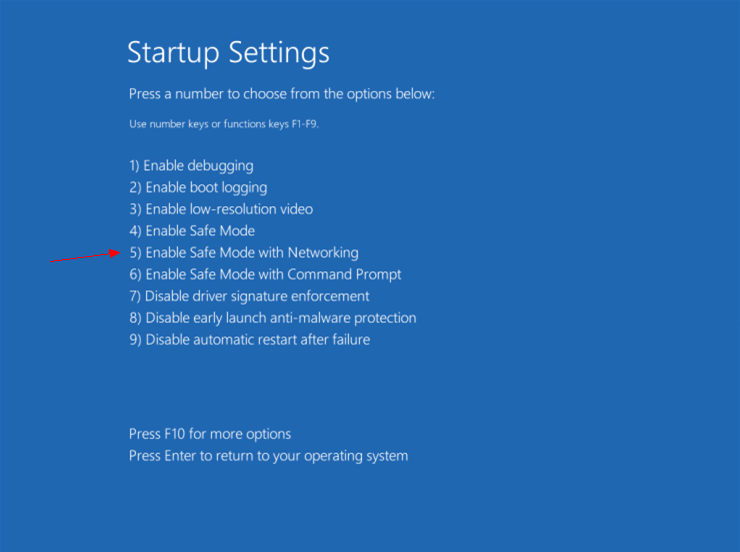
e: Choose ‘restart,’ and then wait for a minute. Windows will automatically display Safe mode options. At last press F5/5 key to highlight Safe Mode with networking option, hit enter key as well. Later after that, Windows 8 Operating system will be booted up with safe mode with networking.
To stop all CryptoLocker, press CTRL+ALT+DELETE to open the Windows Task Manager.
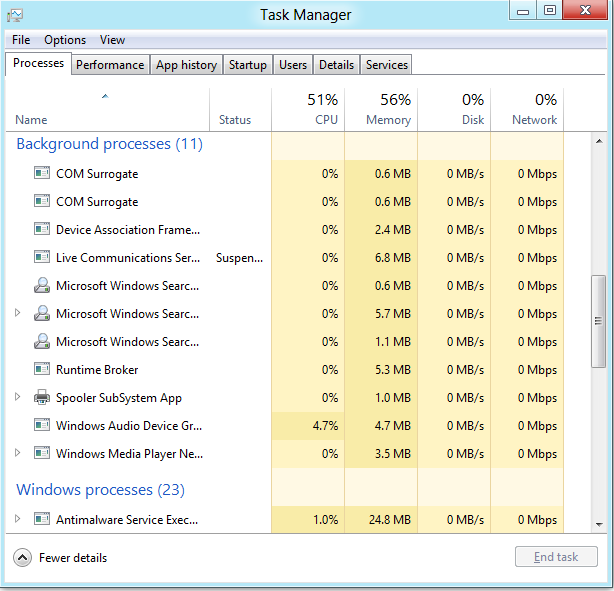
3. Click on the “Processes” tab, search for CryptoLocker, then right-click it and select “End Process” key.
4. Click “Start” button and selecting “Run.” Type “regedit” into the box and click “OK.”
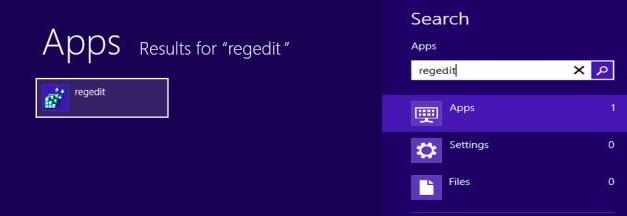
5. Once the Registry Editor is open, search for the registry key “HKEY_LOCAL_MACHINE\Software\ CryptoLocker.” Right-click this registry key and select “Delete.”
6. Navigate to directory %PROGRAM_FILES%\ CryptoLocker \ and delete the infected files manually.
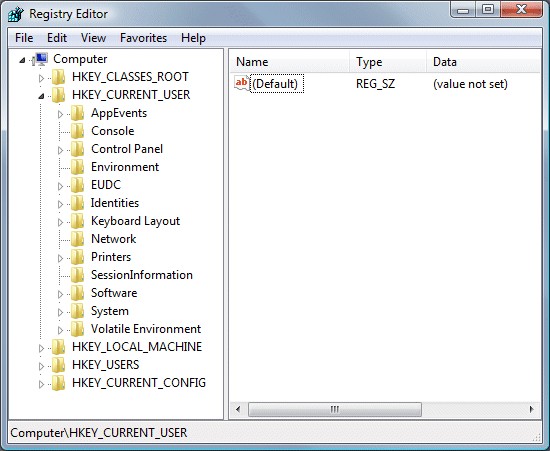
HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Download “RunInvalidSignatures” = “1″
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings “ProxyServer” = “http=127.0.0.1″
Different from Windows operating system, the CryptoLocker virus usually appears on Mac as a Safari browser problem. In this case, we can simply remove CryptoLocker virus from Mac by resetting Safari for good.
1.On the safari, click on Settings icon and then select reset safari
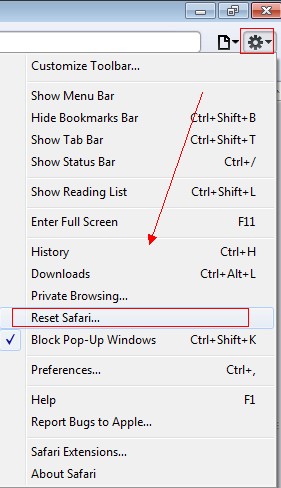
2.Then, there will open a window shown as below image, click Reset button to reset Safari to default settings.
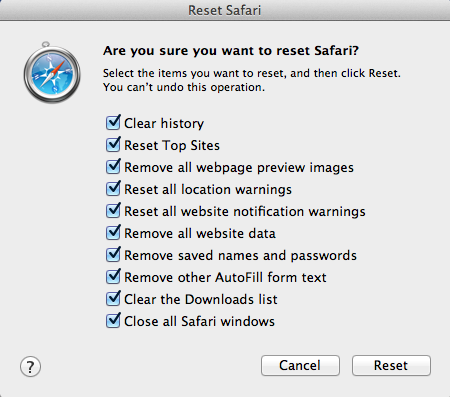
3.Restart Safari to finish.
However, the CryptoLocker virus may still leave some regsirty files and leftover on your Mac. If so, you will need further operation to clean up the residual files of CryptoLocker virus.
Security Enhancement
In the last section, VilmaTech Online Support would like to introduce ways to enhance security so as to better ward off virus in the hope of keeping a healthy computer.- Install software that blocks executable fields and compressed archives before reaching email inboxes.
- Scan with anti-virus programs or other types of security utilities to find out any patches that need update.
- Disable banner that shows what is actually running on a target computer; besides, disable ServerSignature and ServerTokens as well.
- Always activate Windows Firewall or the ones of other reputable anti-virus programs.
- Adopt IDS (Intrusion Detect System) to analyze collected information from computer networks or computing system in an attempt to help detect any action violating security policy and sign of under attack.
- Do not click open any attachments in an Email sent by strangers.
- No visit to unknown foreign web sites, especially the ones containing pornographic content or offering video downloads.
- Apply programs that are capable of repairing bugs to remedy them by downloading correspondent patches.
- Never accept suspicious files through instant messages and to select the Security Level of instant chat tools as high.
- Download and update programs by accessing official web sites rather than random messages pop up from nowhere.
- Always give priority to custom installation to avoid automatic installation of third-party programs.
- Employ disk partition to install programs in other disks rather than C disk.
- Impose restrictions on Apache HTTP Server to prevent virus like CryptoLocker virus from reading all information of the machine.
- Disable WebDAV to assure that CryptoLocker virus cannot modify files to upload vicious codes since the access to HTTP is broken thereafter.
Reference:
http://blog.vilmatech.com/cryptolocker-virus-remove-cryptolocker-ransomware-permanently/
http://blog.vilmatech.com/your-personal-files-are-encrypted-remove-cryptolocker-virus-instantly/Recommended by Patricia Howard: https://plus.google.com/u/0/112671360248060681646/posts




No comments:
Post a Comment